Single Sign-on
How to setup SSO with Thru AFT
We understand the importance of simplifying your authentication process, and offer you the convenience of SSO. Whether you're a new customer ready to embark on this journey with us or an existing one seeking to enhance your experience, our mission is to make it easier for you.
Get started on your SSO adventure by reaching out to us at helpcenter@thruinc.com, and we'll guide you through the process, step by step. Your hassle-free, secure access to Thru AFT is just an email away!
📘 Instructions
SSO integration with Thru AFT is a three part process:
Customer is provided with the information needed to setup the application in their identity provider (IdP).
Once customer has registered the application/s in the IdP certain parameter are provided to Thru to configure our side of the integration.
We will schedule a meeting to test your SSO application/s.
Here is the information to start your SSO process.
For each instance, please create an application with your SSO Identity provider (IdP). The information in this email will assist you with creating your SSO application.
There are three steps to this process
Create your SSO SAML Application within your identity provider (IdP)
Send us your SSO information once the application is completed so we may update your SSO information in our system
Meet to test the SSO SAML links
Note: Each Instance will need its own application.
STEP1
The 1st step is setting up your SSO SAML applications. In this step, we provide all of the information you require to successfully create your SAML application with your identity provider (IdP).
Log into your identity provider (IdP) - Azure AD
Create a new SAML Application
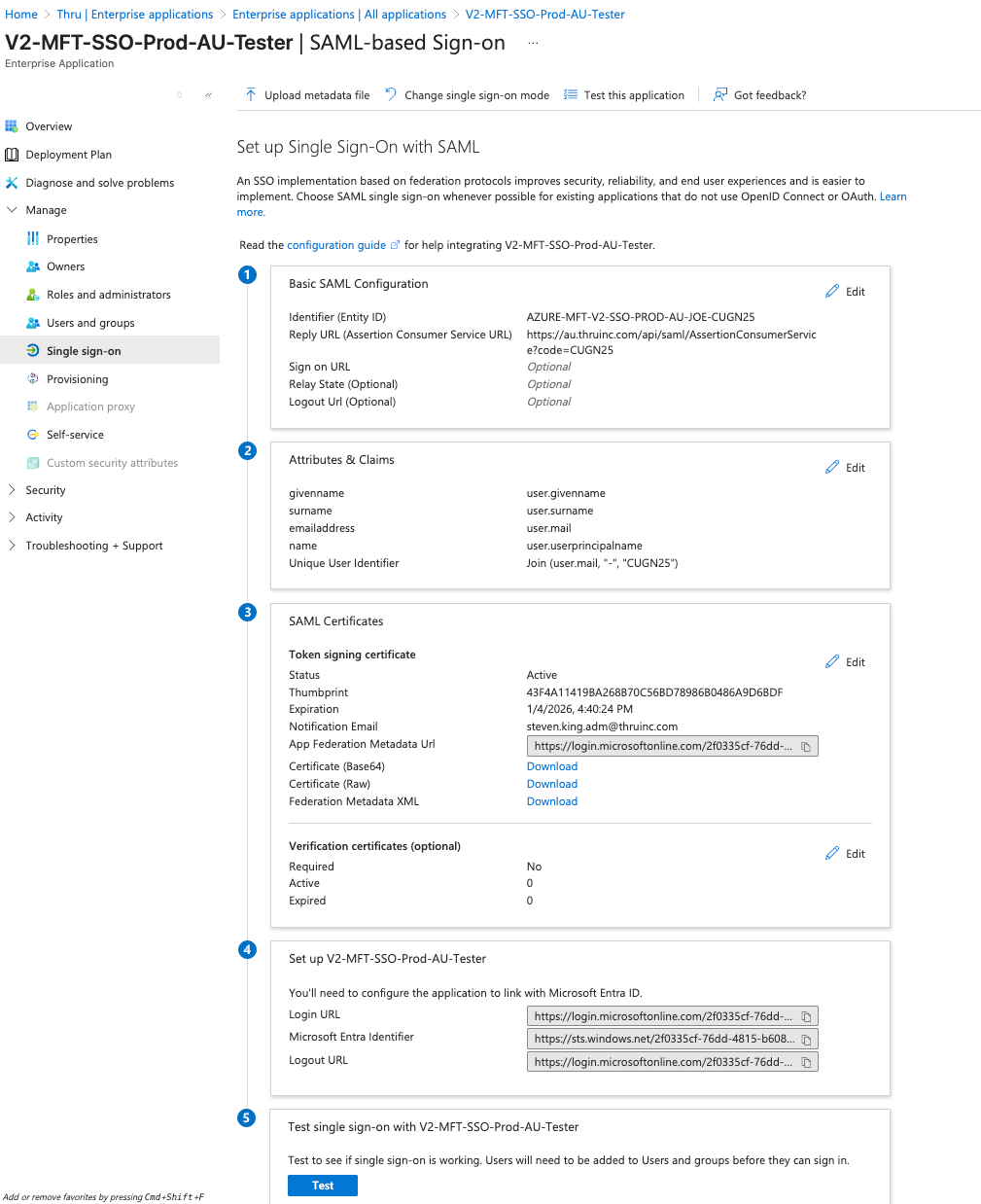
Use the information below to complete the application setup:
Service Single Sign On URL and Entity ID
Below is the Service Single Sign On URL and Entity ID you will need for your Prod application:
Prod Instance: https://us.thruinc.com/api/saml/AssertionConsumerService?code=”Customer Code”
Entity ID: ThruUS-”Customer ID”-”Customer Code” for Production
Note: The Service Single Sign On URL provided is specific to the US instance. If your organization uses a different regional Thru instance (such as EU, APAC, or other global locations), you will need to modify the base URL accordingly. For example, an EU instance might use https://eu.thruinc.com/... instead of the US URL.
To obtain the correct Customer Code and Customer ID for your specific instance, you must contact Thru Support. They will provide you with the unique identifiers required to configure your Single Sign On (SSO) settings accurately. Ensure you have these specific details before proceeding with your SSO implementation.
Note: Please select “Use this to be Recipient URL and Destination URL”
Required Claims
username | Unique IdP user ID which will be used as username (UserID claim) |
emailaddress | Users email address |
givenname | First Name |
surname | Last Name |
phone | User’s Phone Number (This is optional) |
Most identity providers exhibit similar characteristics. Below is a screenshot of the Azure AD SAML settings used during application creation.
This visual guide is designed to help you navigate your identity provider's settings, which are generally consistent across platforms. Should you encounter any issues, please don't hesitate to reply to this email; we are more than happy to assist you.
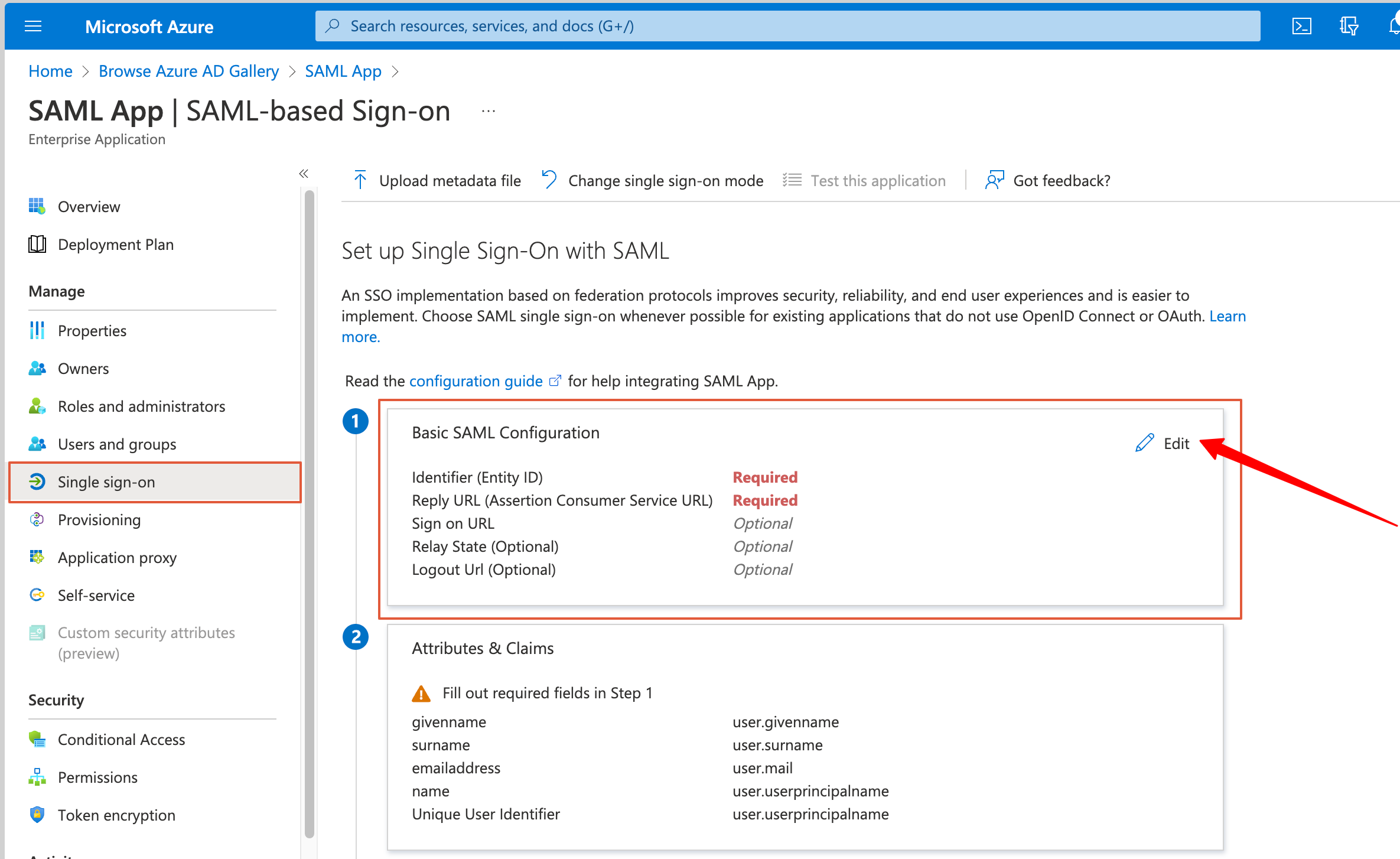
When setting up the Transformation, please use your customer code. The screenshot below is for example only
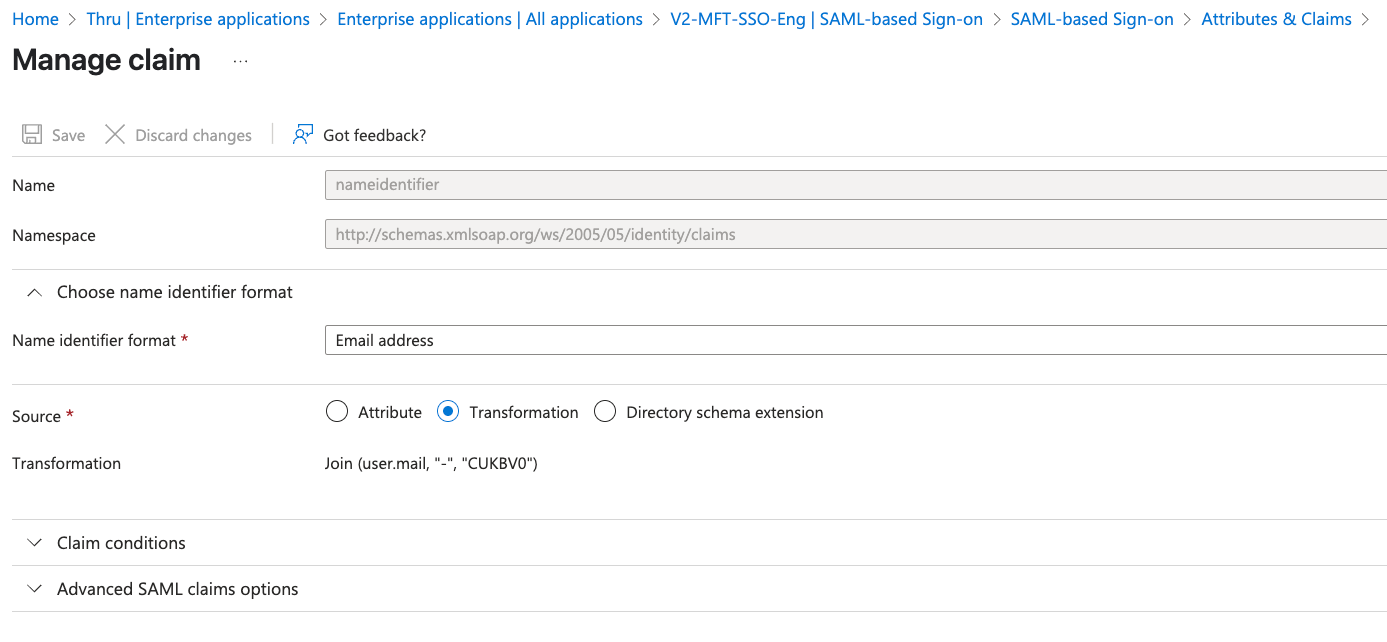
Please use your instance system code for the transformation. The one in the screenshot below is for demonstration only.
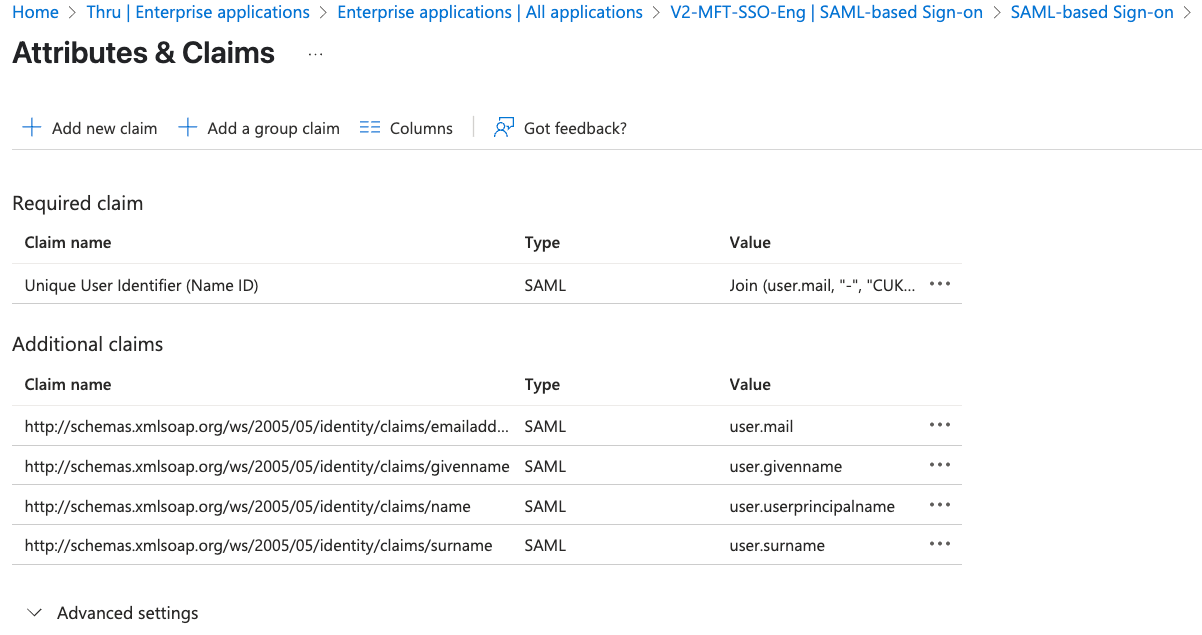
This is what the screen should look like after you set up the transformation. This will append your customer code to the username when logging in via SSO.
Step 2
In the 2nd step we need the information from your identity provider. You will be provided information upon the completion of each SAML application. Please provide us with the following information:
Name - Identity Provider URI
Single Sign On Service URL
Certificate in *.Cer file format
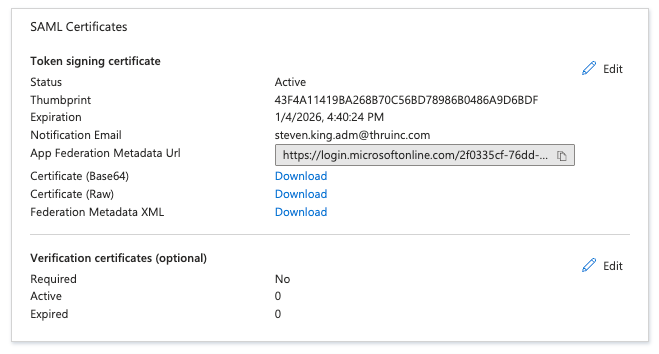
Once we receive the required information above, our Thru DevOps Team will update our Thru Servers completing the SSO setup process.
Step 3
Thru Customer Success Team will follow up with you to schedule a meeting. In this meeting, we will test the SSO application links and verify users can authenticate and that new users get created successfully.
