Thru Server Endpoints
Thru Server endpoints depict situations where Thru operates as a server, offering a platform for users, systems, or applications to engage with us as clients.
Upon endpoint creation for the organization, Thru generates an URL (host) for connection establishment.
For users opting to utilize a Thru Server endpoint, an associated user account must also be generated to gain access to the Thru server.
In this example, we will set up a source Thru SFTP endpoint and create a user to upload files.
Click the Organization tab.
On the Organization you just created, hover over the Actions tab icon and select Endpoints.
Click the + Add Endpoint button.
Toggle to Disable. (if required)
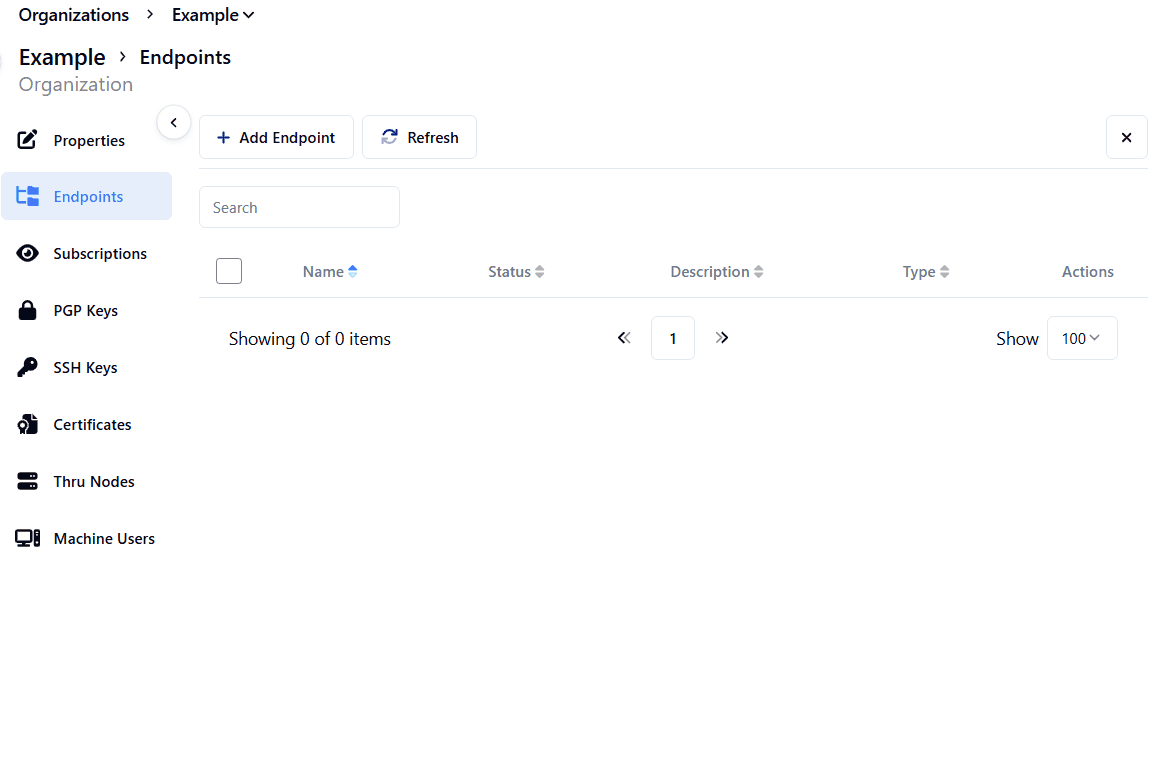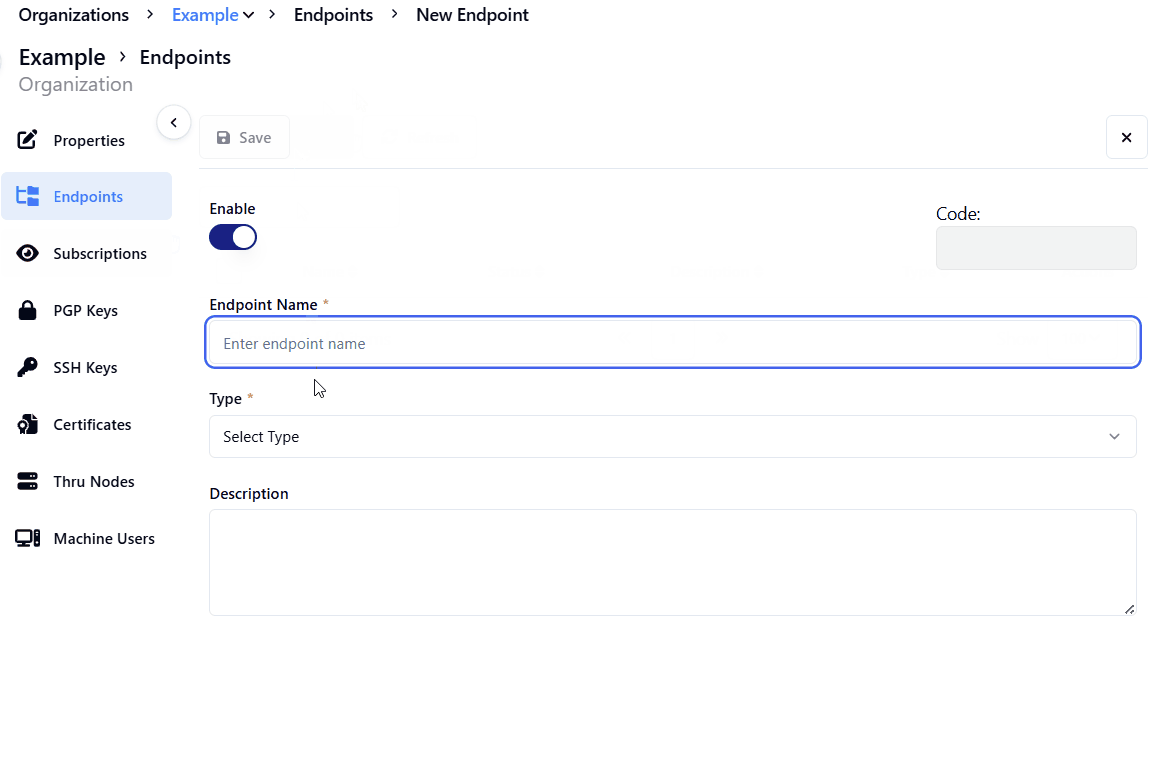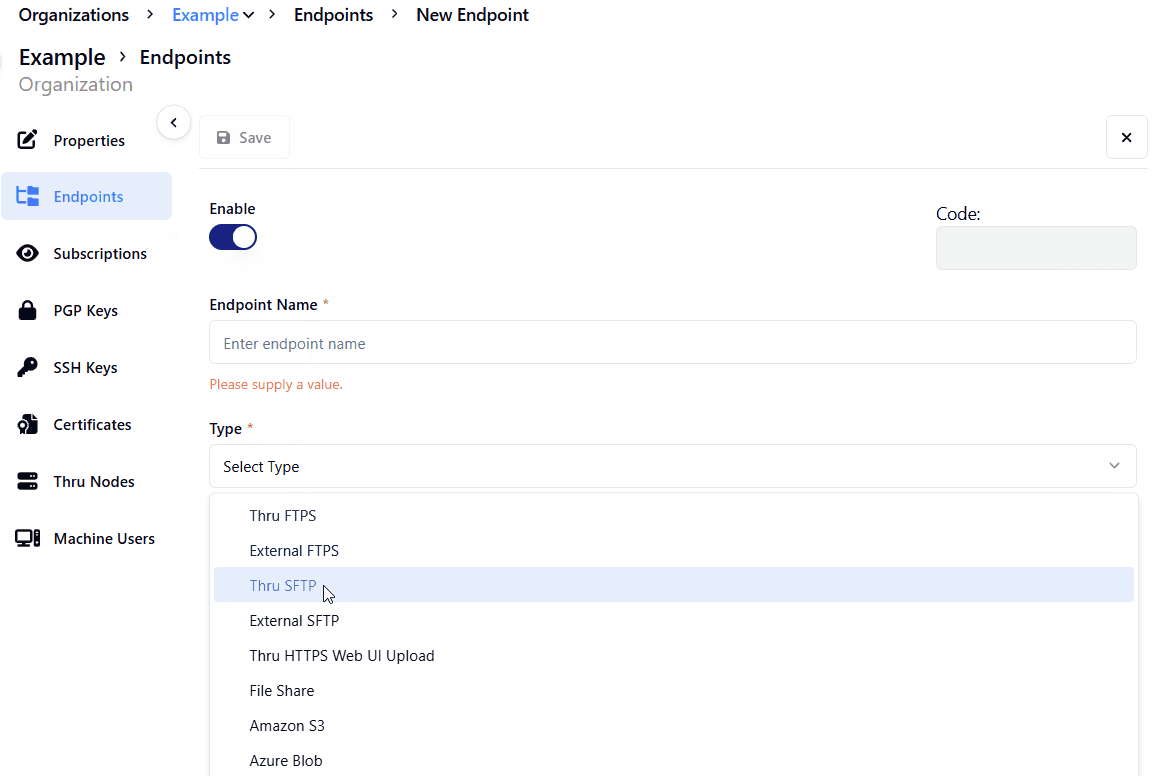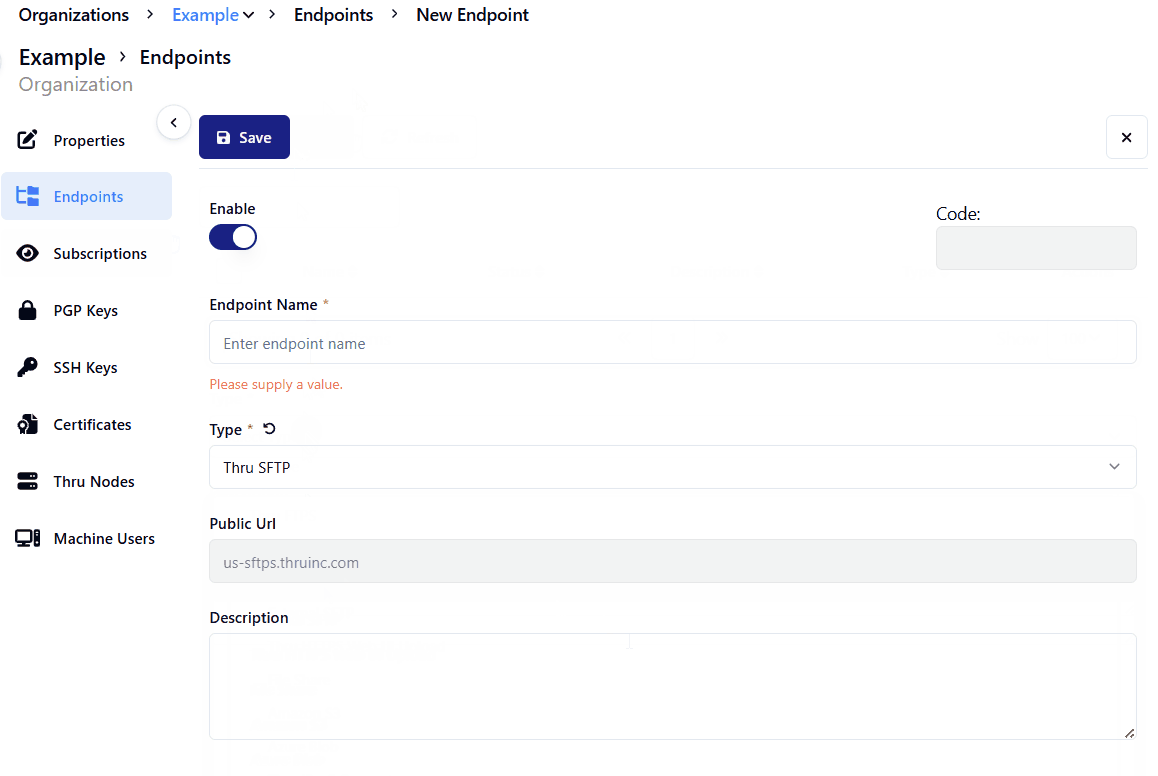
Click on Select Type for the Type * field.
Select Thru SFTP Server from the dropdown.
Enter a description for the Endpoint.
Click the Save button.
Trigger files are required to prevent partial files when using Thru Server endpoints.
Add the Endpoint to a Flow
Navigate to Flows and select a flow. This will automatically land you in Flow Studio.
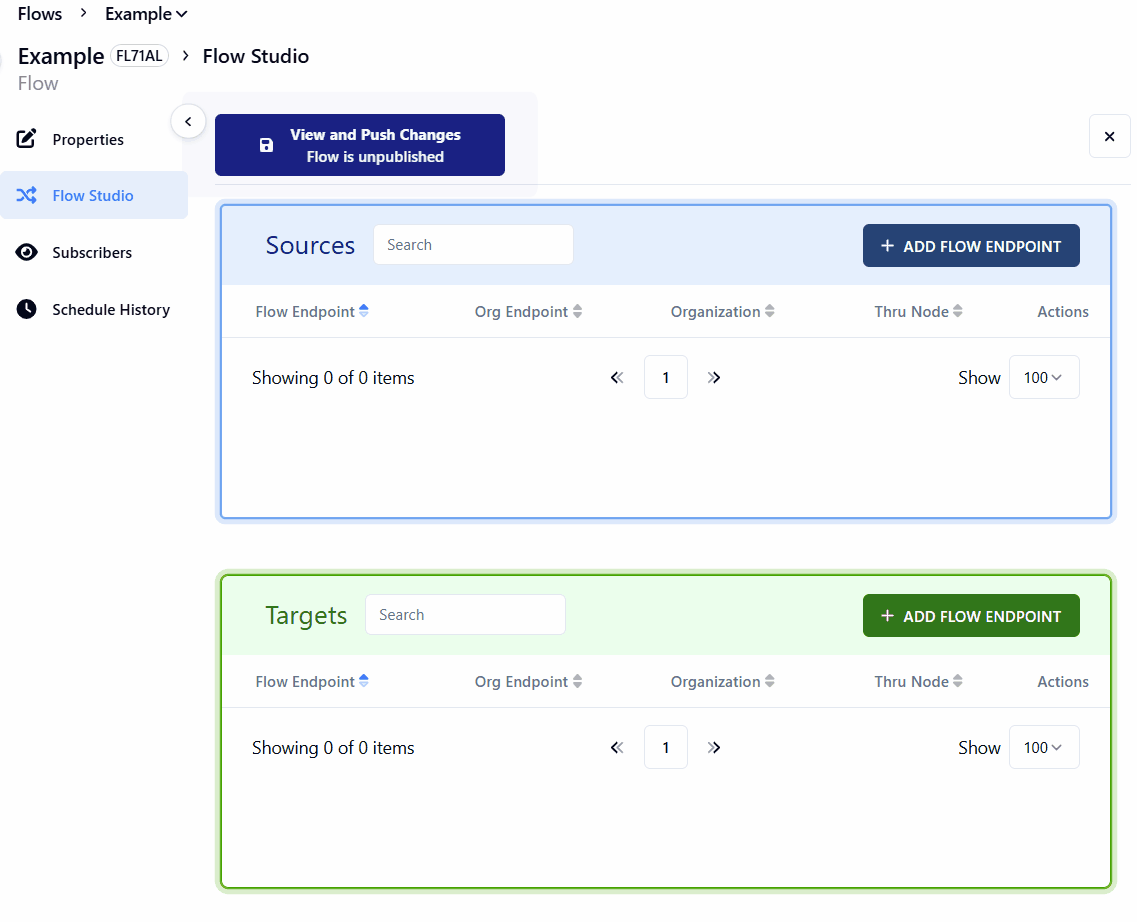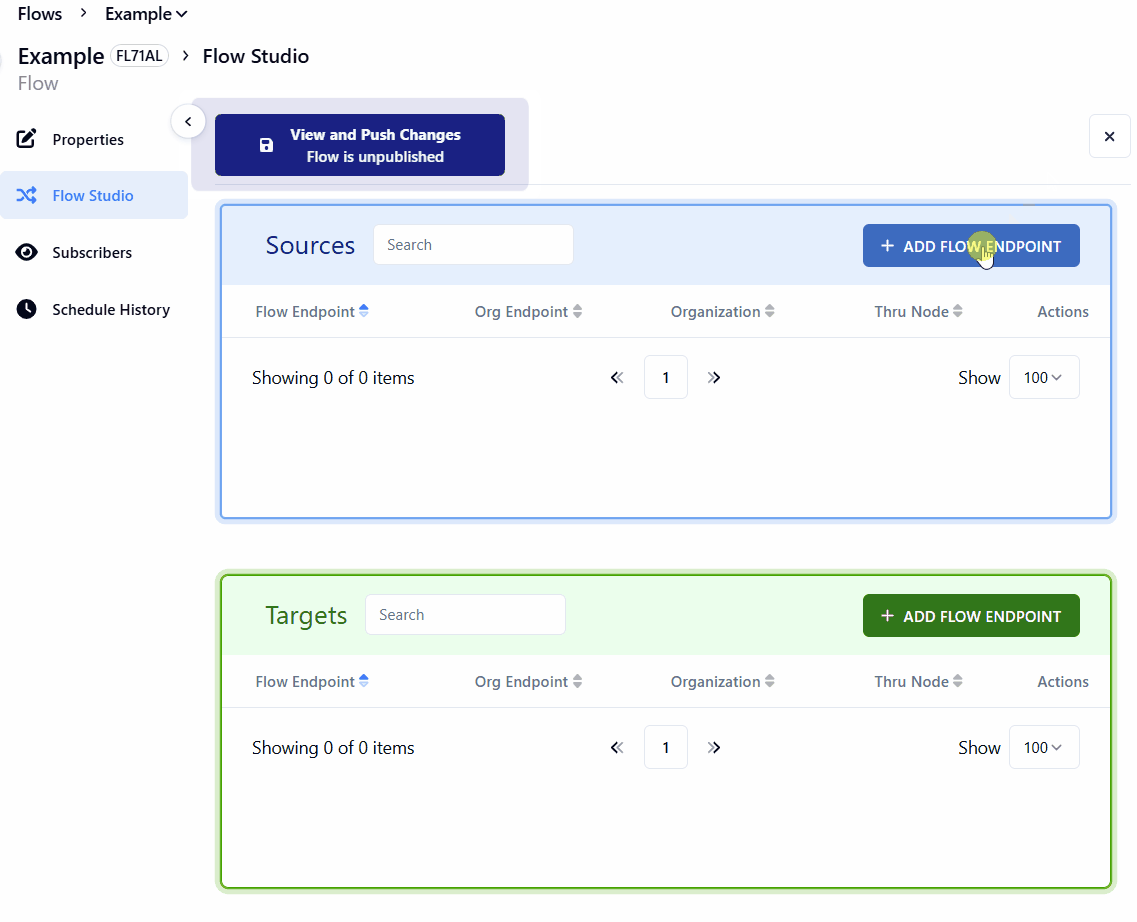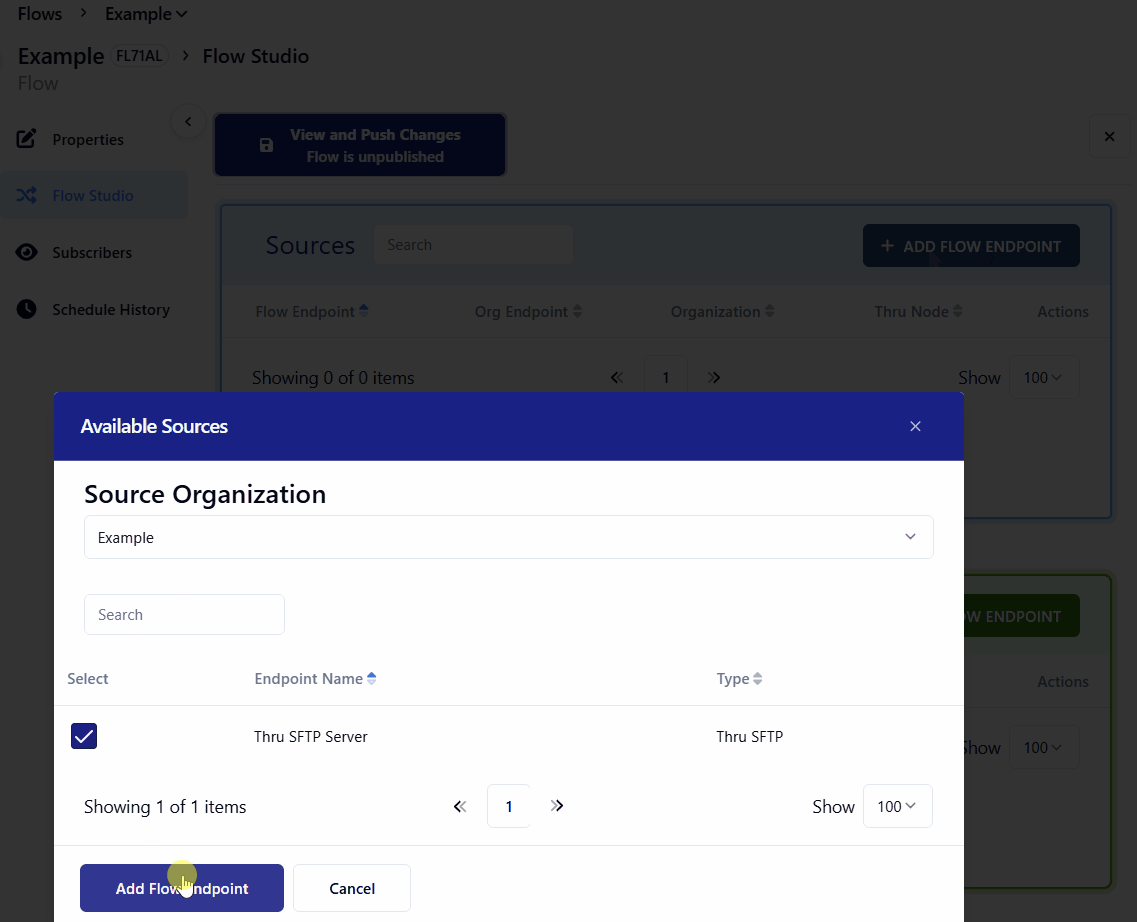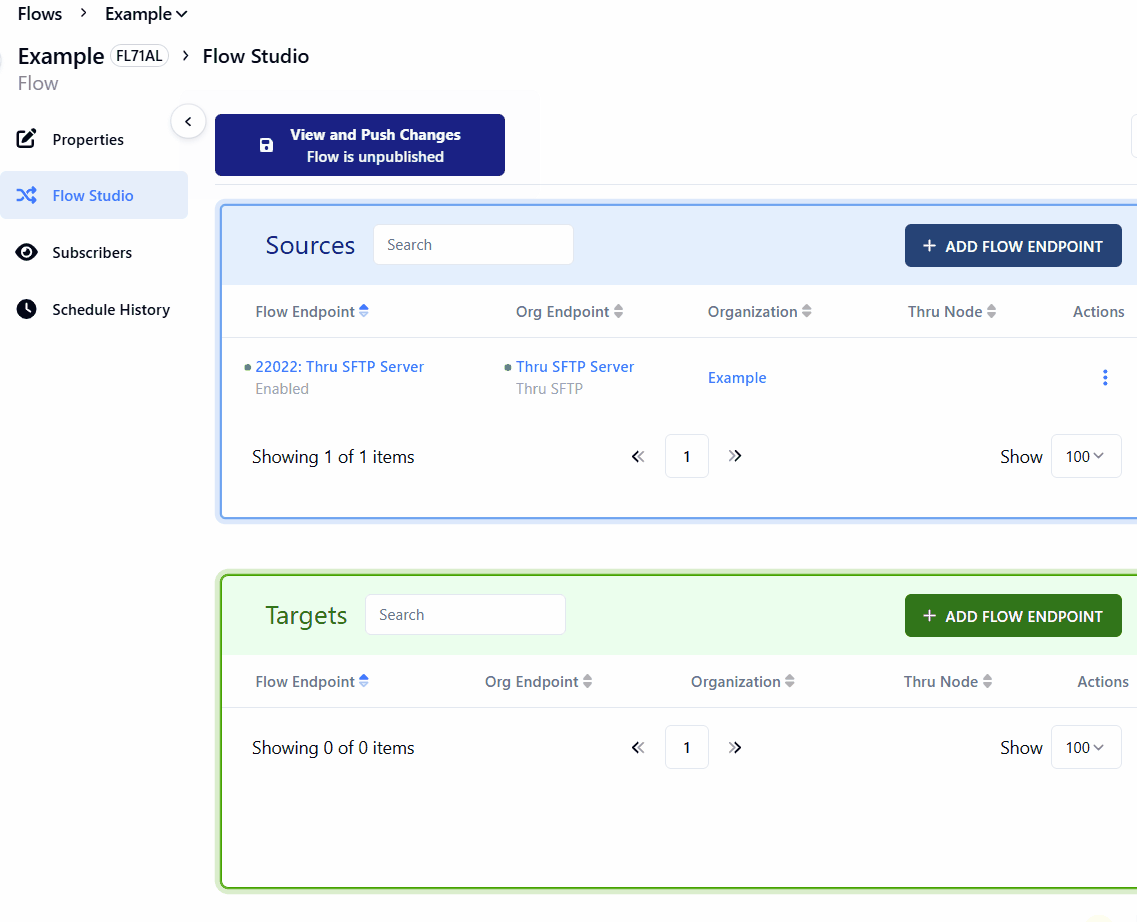
Click + ADD FLOW ENDPOINT and select the endpoint which was created in the last section.
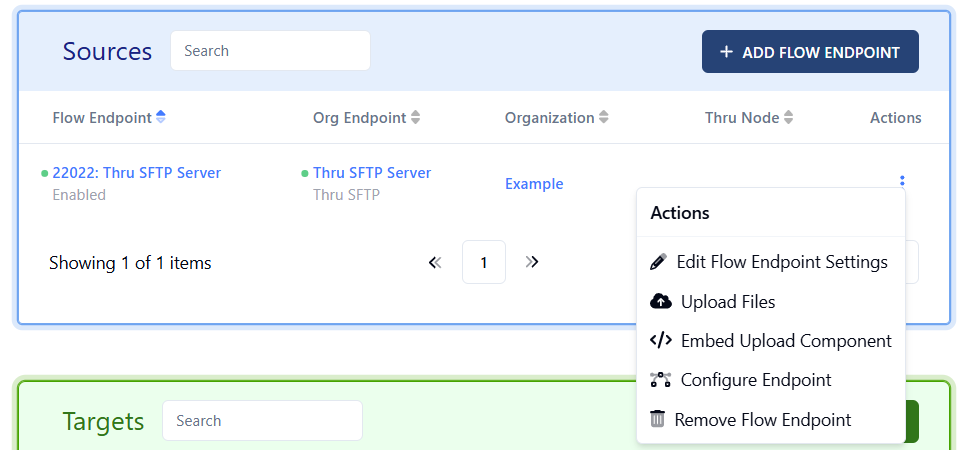
Now using the Actions icon, select Edit Flow Endpoint Settings.
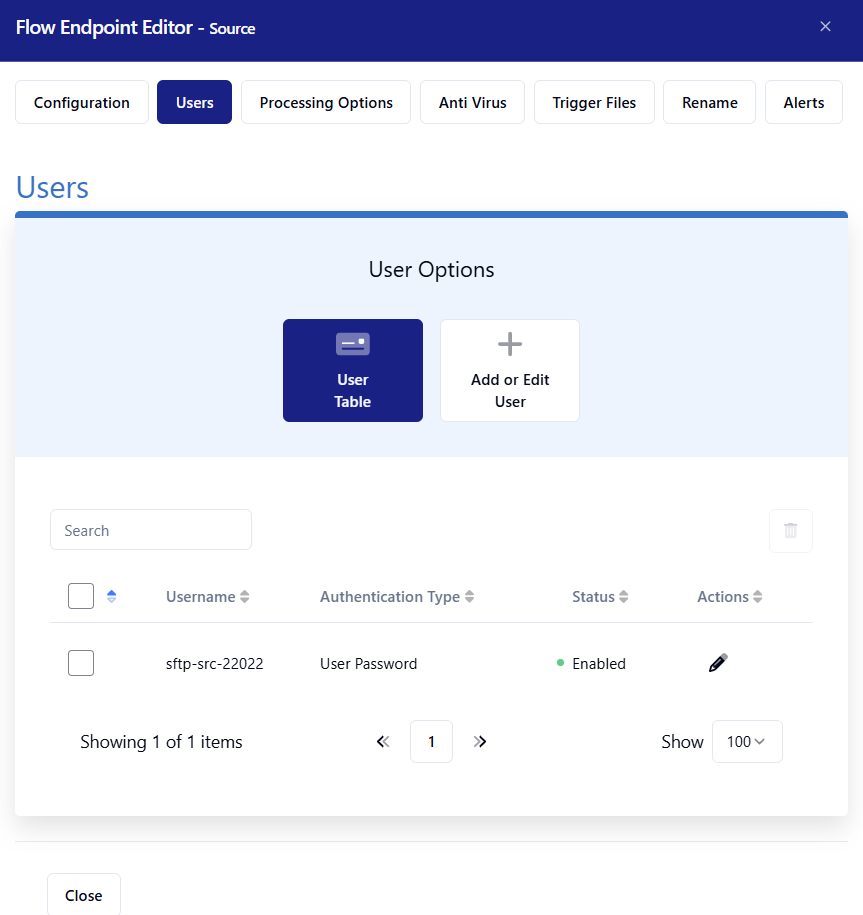
Add User
Click the Flows tab.
Select the Flow you want to use.
Click the tri dot icon under Actions and select Edit Flow Endpoint Settings for the endpoint.
Click the Users tab.
Click + Add or Edit User.
Enter a username in the Username * field.
Select which Authentication Type *, we will use User Password.
Enter a password in the Password * field.
Click Save.
Thru can create a user automatically, this user can be used, edited or deleted. See Feature Flags
Requiring unique user accounts for source and target SFTP/FTPS endpoints is a security best practice that helps mitigate risks and enhance the overall security posture of file transfer operations. Here's a valid reason for this practice:
Isolation and Least Privilege: Requiring unique user accounts for both source and target SFTP/FTPS endpoints follows the principle of least privilege and isolation. Each SFTP/FTPS endpoint, whether it's the source or the target, should have its own dedicated user account with the minimum necessary permissions to perform its specific role. This ensures that if a breach or unauthorized access occurs on one endpoint, the attacker's ability to move laterally within the environment is limited. It prevents a compromised account on one endpoint from directly affecting the other.
For instance, if a shared user account was used for both source and target endpoints, an attacker who gains access to that account (or compromises the password) would have unfettered access to both sides of the file transfer. With separate accounts, the attacker's ability to propagate their access is constrained, reducing the potential impact of a security breach.
Furthermore, this practice also aids in auditing and accountability. With unique user accounts, it becomes easier to track and attribute actions to specific individuals or processes, making it simpler to identify the source of any security incidents or breaches.
In summary, using unique user accounts for source and target SFTP/FTPS endpoints enhances security by enforcing isolation, limiting lateral movement, and adhering to the principle of least privilege, all of which contribute to a more robust and secure file transfer process.
