Azure Blob - External Identity Provider Authentication
Overview
Two new authentication options are being introduced for Azure Blob Storage access:
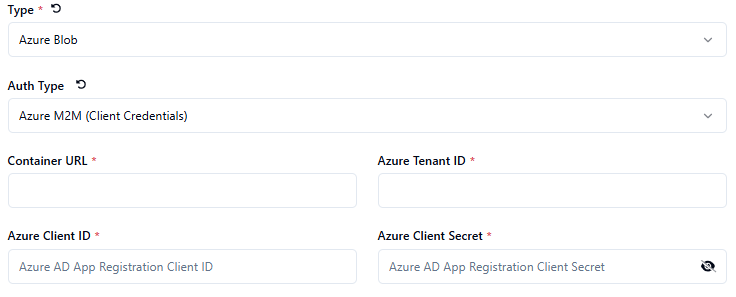
Azure Machine/Client Credentials - Direct communication with Azure and blob storage
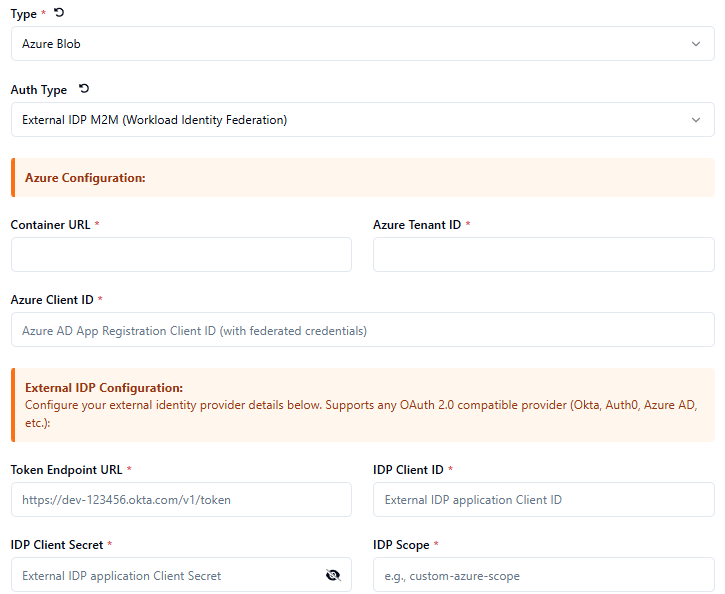
External Identity Provider Authentication - Authentication through external providers like Okta or Auth0
Key Features
External Identity Provider Flow
Customers provide Azure tenant ID and application ID (registered in Azure AD)
No secret sharing required - authentication handled through external identity provider
Token exchange process: External IDP token → Azure token → Blob storage access
Uses federated identity credentials in Azure
Supported Providers
Okta (primary testing done with this)
Auth0
Other external identity providers (potentially)
Configuration Requirements
Okta Configuration
Register application in Okta
Configure API/Authorization server in Okta
Set up token endpoint and metadata URL
Application should use private key authentication (not client secret - this is disabled/not supported)
Default token settings can be used (no special grant types needed)
Azure Configuration
Register application in Azure AD
Configure federated identity credentials
Link Okta application to Azure application via:
Issuer URL (from Okta)
Application ID (from Okta)
Audience configuration
Required Azure Permissions
Two roles needed for the registered application:
Storage Blob Data Contributor - For data operations (upload/download/listing)
Storage Account Contributor OR Reader - For accessing storage properties and metadata
Note: Reader role may be sufficient instead of Storage Account Contributor for metadata operations
Technical Implementation
Token Management
Uses Microsoft library for Azure communication
Automatic token refresh handling
Checks token expiration before each API call
Refreshes token if less than 5 minutes remaining
Based on client credential flow (no refresh tokens)
Default token lifetime: 1 hour (configurable via policy)
Customer Benefits
Enhanced Security - No need to share Azure credentials directly
Centralized Access Management - Customers can manage access through their existing identity provider
Quick Access Control - Can disable access centrally through their IDP without touching individual services
Simplified Credential Management - Reduces credential sprawl
Customer Responsibilities
Configure their Okta/external IDP
Register application in their Azure subscription
Assign appropriate roles to the application
Provide configuration details (tenant ID, application ID, token endpoints)
