Thru SFTP Server
Secure Shell File Transfer Protocol (SFTP) is a network protocol used for the secure transfer of data over the internet. SFTP leverages the full security and authentication features of the Secure Shell (SSH) protocol. This makes it well-suited for exchanging sensitive data between business partners in industries such as finance, healthcare, retail, and advertising. SFTP provides a robust and encrypted means of transferring files, ensuring the confidentiality and integrity of the data being shared. Its widespread adoption across various sectors highlights the importance of secure data transmission in today's interconnected business landscape.
Thru SFTP servers operate over port 22
To create a Thru SFTP Server Endpoint:
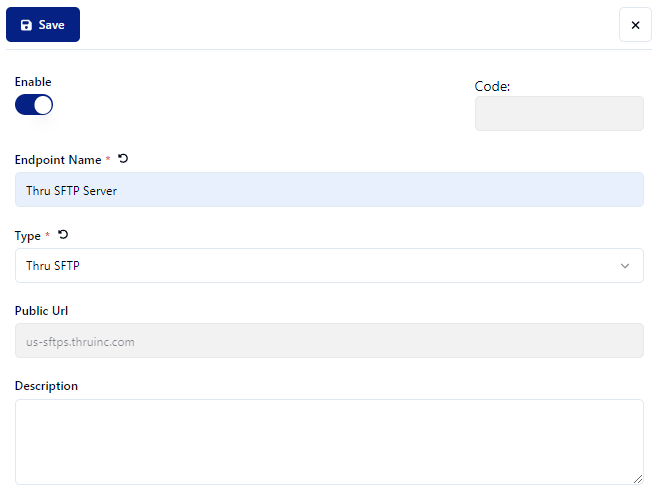
Click Organizations.
Select an organization.
Click Endpoints.
Click the + Add Endpoint button.
Enter the name in the Endpoint Name * field.
Select Thru SFTP Server protocol from the Type * drop-down.
Note the example Public Url in order to make the connection.
Enter a description for the endpoint.
Click the Save button.
After incorporating this endpoint type into a flow, the ability to create user accounts is available from within the Flow Endpoint.
Resume
The file transfer feature of Thru SFTP Servers necessitates the following requirements:
Trigger files
The client must utilise 'binary' transfer mode
Post-upload operations
Thru does not allow post-upload operations on Thru SFTP internal sources unless the client software employs a temporary file name. This temporary file name must also be set up in the Thru SFTP source's internal flow endpoint, located under the Triggers tab.
Idleness
Thru SFTP assesses the idleness of SFTP sessions by monitoring the time since the last command was received. If an SFTP connection remains open without any command being sent for over 15 minutes (the default timeout), the session will automatically close. To maintain an active SFTP session, it is essential to periodically send a command. For instance, you can request the current directory to keep the session alive.
Whitelisting
All inbound IPs connecting to Thru’s SFTP service must be whitelisted. For further information, please refer to the following link.
SFTP (SSH) Host Key
Thru's SFTP SSH host key details can be found at the following link.
SSH
Using a shell is prohibited because it is frequently exploited for malicious purposes. Additionally, a shell does not serve any function in the context of file transfer.
